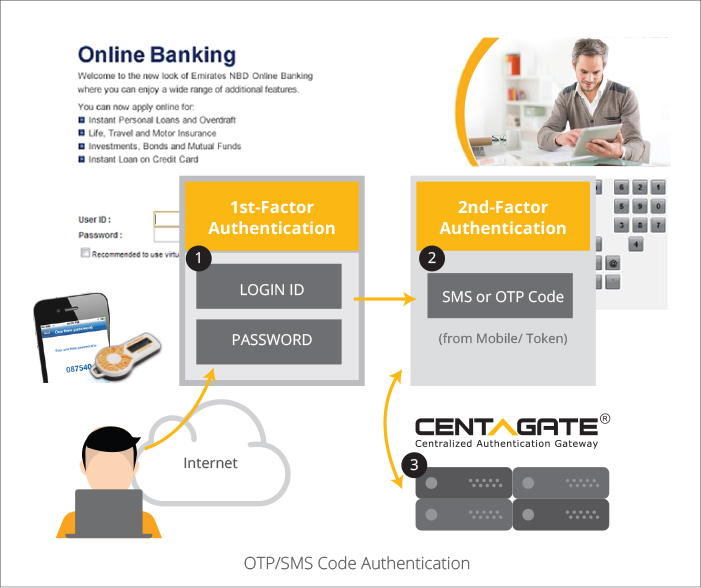
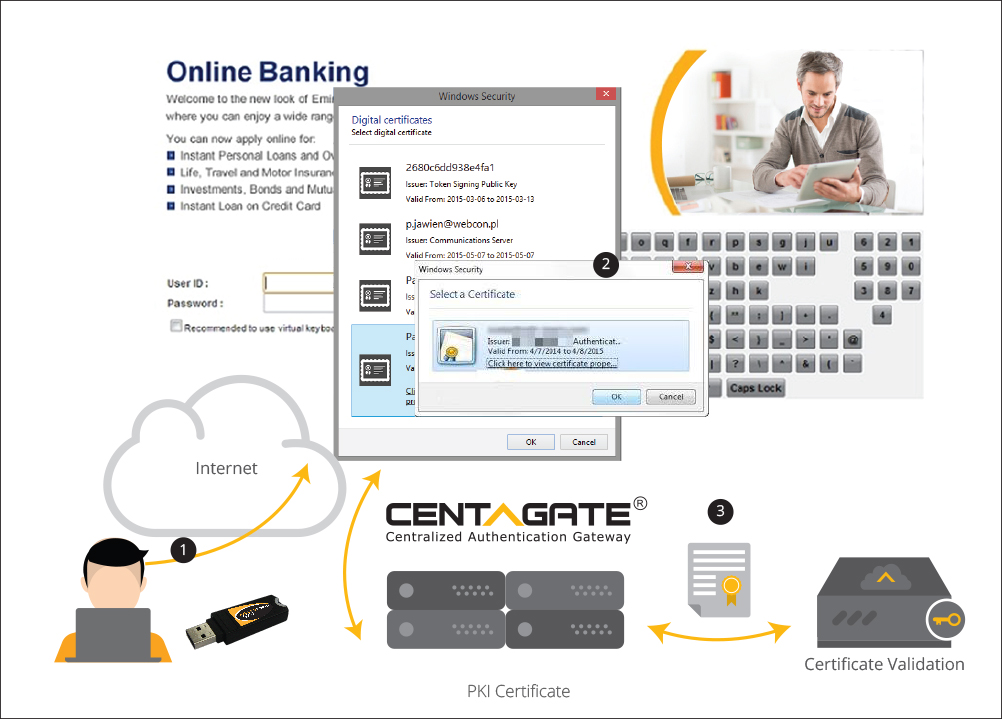
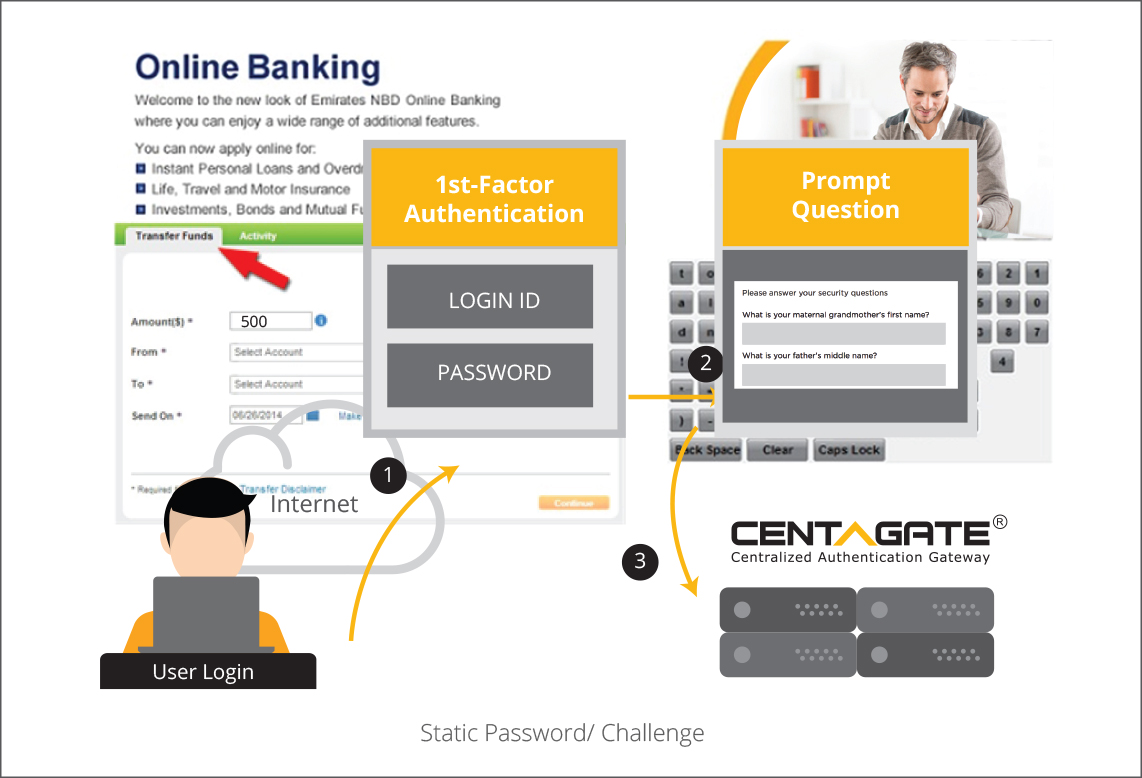
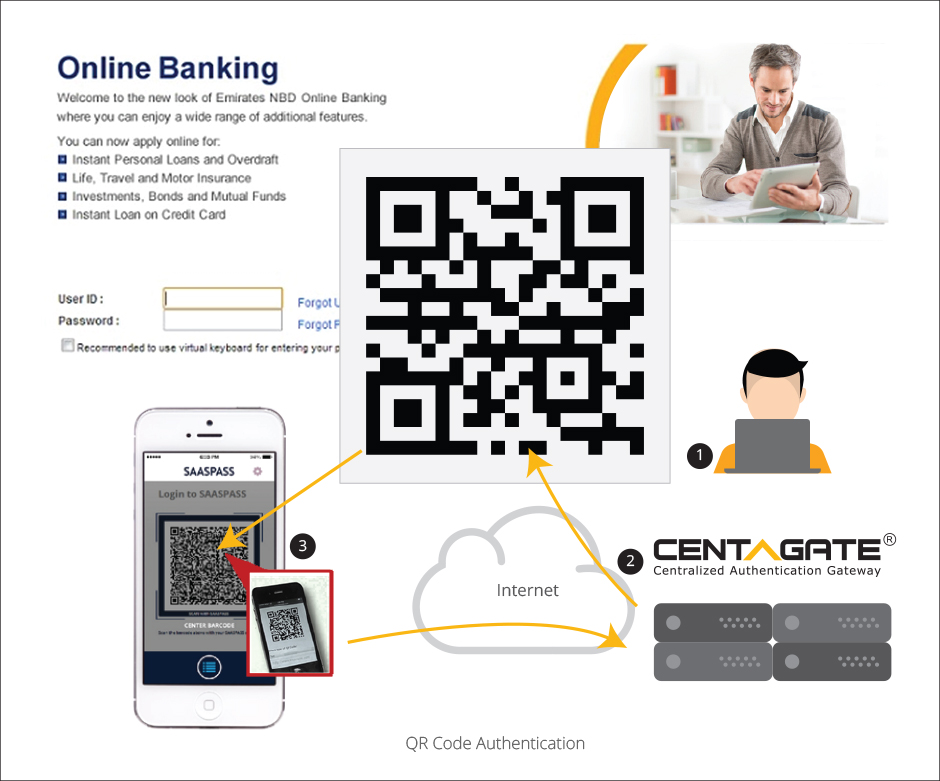
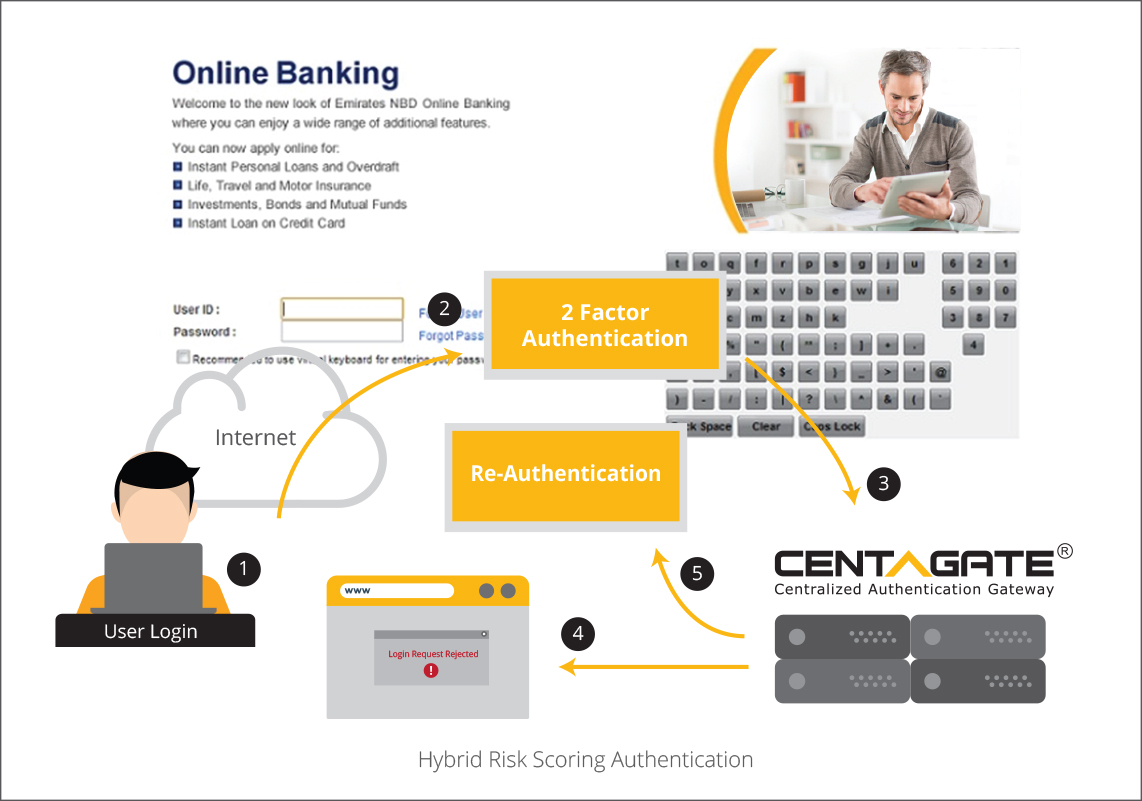
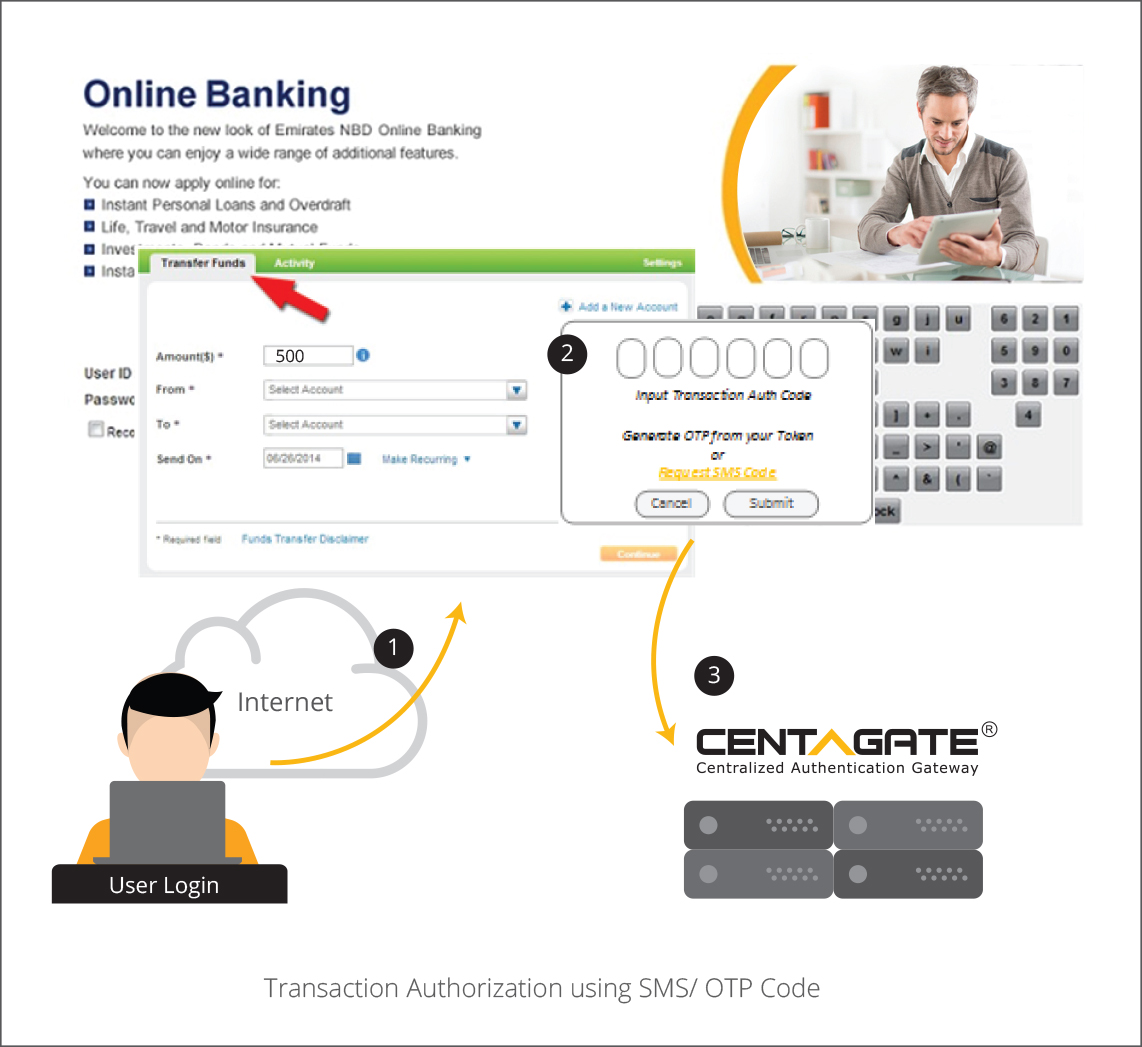
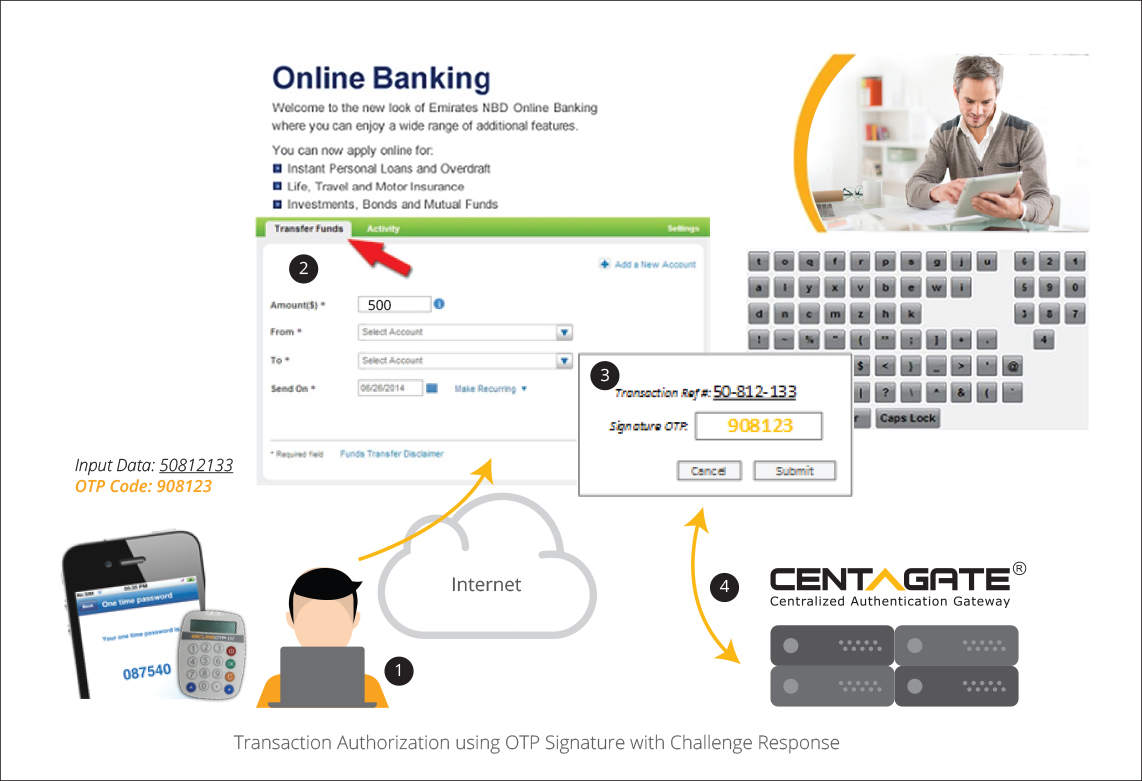
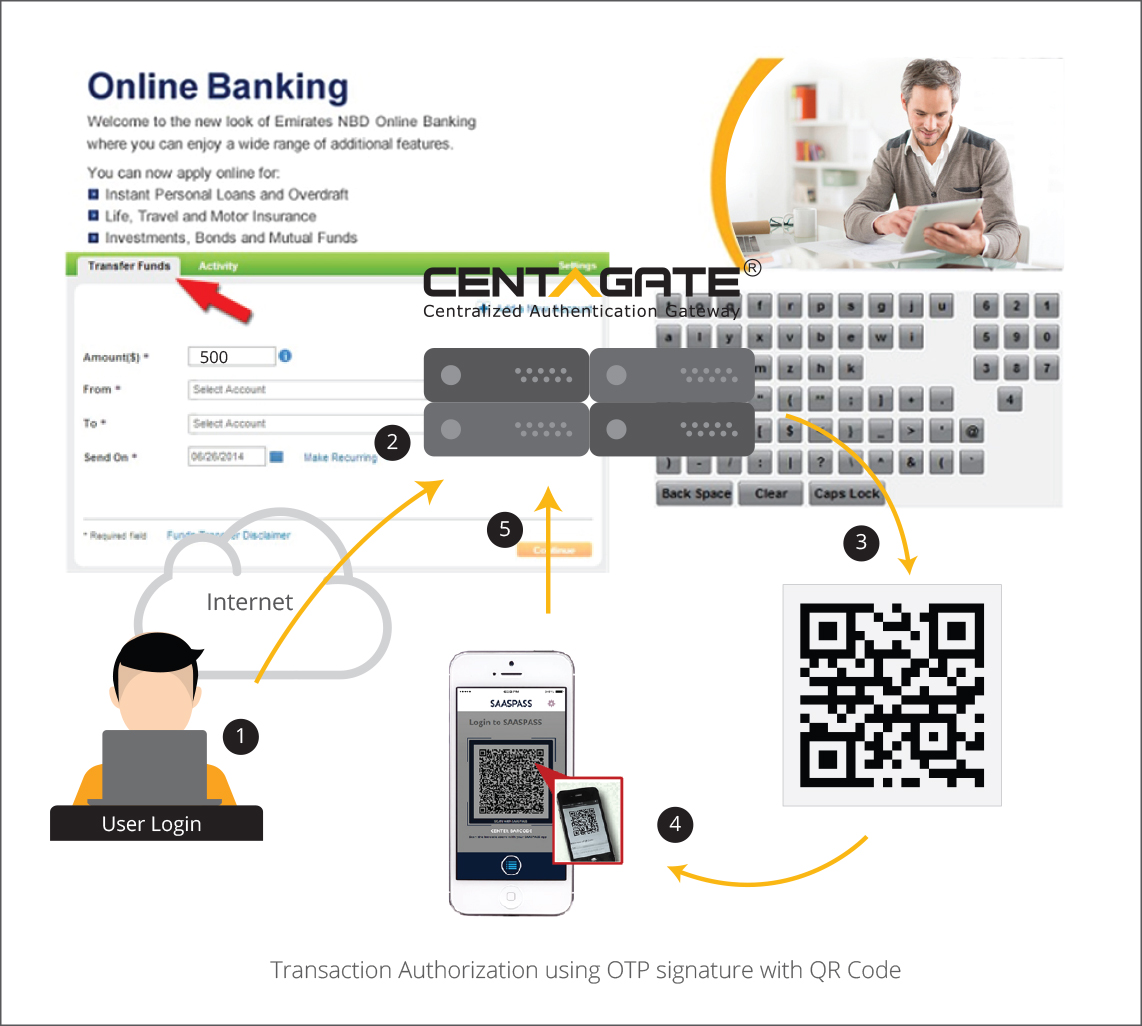
D. QR Code Authentication

Protect login to client application with local password and QR Code generated by CENTAGATE®.
Integration: Web Services/ SSO.
Application type: Web based applications, SAML2.0 compliant devices/applications
Flow:
(1) The client application validates the “Login ID” and “password, when successful, it will call API to request QR code from CENTAGATE®.
(2) CENTAGATE® generates QR code which will be displayed on the client application page.
(3) User with mobile app will use “QR code” scanner to authenticate with CENTAGATE®. When successful, user is allowed to access the application.
Note: If using QR code, the user must have a registered/linked mobile device with CENTAGATE® mobile app installed or integrated.
During authentication, the mobile device/app must have online/internet connectivity.